Version 2 commands : cryptography edition
You may be curious about the meaning of "version 2". This refers to the second iteration of our cryptography commands, which are closely interconnected with one another. Please find a detailed explanation of these commands below.
37. Encode command
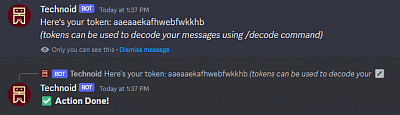
This command functions similarly to the "/encrypt" command, in that it encrypts the user's text. However, instead of providing an abundance of information such as key and filename, it generates a secure token that can be used to access the encrypted text at a later time. This token provides the same level of security as the aforementioned information, ensuring that the user's data is always protected.
38. Decode command
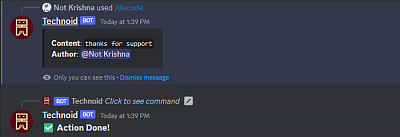
This command is akin to the "/decrypt" command, as it decodes encrypted messages using a token. However, unlike the "/decrypt" command, this command does not delete the message after decoding. Instead, the message will remain in the repository until the author decides to explicitly delete it.
39. Cipherlist command
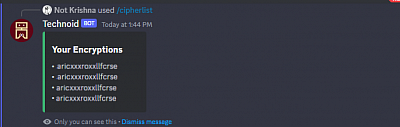
We have implemented a command to assist you in case you forget your token. By running this command, you will receive a list of encrypted tokens that belong to you.
40. Cryptoshred command
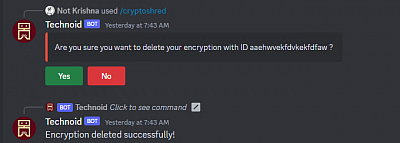
Lastly we have successfully developed a command that enables you to delete an encryption by providing the corresponding token as an argument. Please note that only the author of the encryption has the authorization to perform this action, hence you do not need to worry about unauthorized deletions.